
Setup Page – Software Deployment Options & Preferences

Setup Page – Software Deployment Options & Preferences
Table of Contents
- Introduction
- Registration
- Using Advanced Installer
- GUI
- Working with Projects
- Installer Project
* Product Information
* Product Details
* Digital Signature
* Digital Signature Settings Tab
* Files Configured for Signing Tab
* Updater
* Upgrades
* Licensing Page
* CD/DVD Autorun
* Multiple Instances Page
* Resources
* Package Definition
* Requirements
* User Interface
* System Changes
* Server
* Custom Behavior - Patch Project
- Merge Module Project
- Updates Configuration Project
- Windows Store App Project
- Modification Package Project
- Optional Package Project
- Windows Mobile CAB Projects
- Visual Studio Extension Project
- Software Installer Wizards - Advanced Installer
- Visual Studio integration
- Alternative to AdminStudio/Wise
- Replace Wise
- Migrating from Visual Studio Installer
- Keyboard Shortcuts
- Shell Integration
- Command Line
- Advanced Installer PowerShell Automation Interfaces
- Features and Functionality
- Tutorials
- Samples
- How-tos
- FAQs
- Windows Installer
- Deployment Technologies
- IT Pro
- MSIX
- Video Tutorials
- Advanced Installer Blog
- Table of Contents
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
Settings Tab - Installer Project
In this tab you can configure the digital signature of your package.
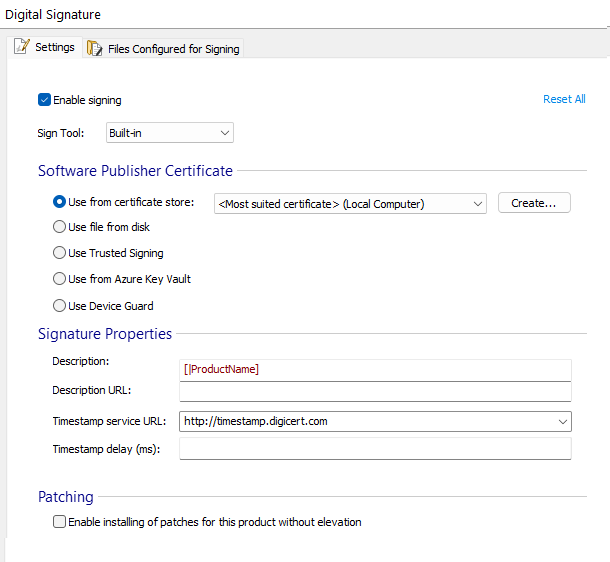
Enable signing
Checking this checkbox will enable the actual signing of the package.
Reset All
This button can be used to clear all fields.
Signing Tool
Built-in
Use the built-in signing tool.
Custom
Path:
Select a custom signing tool.
Command Line:
Enter a command line for the above cutom signing tool.
Environment variables can be specified in Command Line field and they can be referenced as %ENV%.
Software Publisher Certificate
Use from certificate store
Choose one of the currently installed certificates.
Only certificates from “Current User\Personal” store are imported in “Use from certificate store”.
Command line examples:
signtool sign /a /d <desc.> /t “http://timestamp.digicert.com “
Copy
To view or manage certificates inside the system store, you can usecertmgr.msc tool (Press Windows Key +R, type “certmgr.msc” and press enter).
[Create… ] - Creates a certificate with which you can sign your package for testing. Make sure you install it as a trusted certificate and use it only for testing purposes.
Use file from disk
When this option is selected the certificate used to sign the files is loaded from a local disk file. Every time you select this option, you will be prompted to select the path to the certificate from the hard-drive.
Advanced Installer supports both Personal Information Exchange PKCS #12 (.pfx) and X509 (.cer) certificates.The .pfx certificates contain both the public and private keys. The .cer certificates contain only the public key, the private key being stored onto an USB eToken (protected by password).
Certificate - This field contains the path on disk to the certificate. You can use the [… ] button in this field to select one from your hard-drive.
PFX certificates are recommended, you can use either pvkimprt or pvk2pfx to create a PFX certificate from the SPC and PVK files. If the PFX file is protected with a password, the “Selected certificate requires password. Select how to transmit it to signing tool:” section will be visible.
- pvkimprt can be downloaded
- pvk2pfx is available as part of the Platform SDK
Private Key - In this field you can set the “Private Key”. You can use the [… ] button to select one from your hard-drive. PFX certificates do not have a separate private key file; thus this field is hidden by default.
Enter password each time project is built - You will be prompted to enter the password when the MSI is built.
Advanced Installer caches the password for PFX files; thus you will be prompted for the password only once.
Store encrypted password in project file - The encrypted password will be stored in the project and used at build time to sign the installation files. This option is useful for unattended builds.
Password - The password for the PFX certificate.
Confirm password - Confirm the PFX certificate password.
Command line examples:
signtool sign /f
Copy
signtool sign /f
Copy
Use Trusted Signing
To use this option you need to own a Microsoft Azure subscription with Trusted Signing configured.
End Point
Specify a URI value that aligns to the region your Code Signing Account and Certificate Profile were created in during the setup of these resources.
Account Name
Specify the Code Signing Account name.
Certificate Name
Specify the Certificate Profile name.
Correlation ID
In this optional field you can specify an opaque string value that you can provide to correlate sign requests with your own workflows such as build identifiers or machine names.
Use from Azure Key Vault
To better understand this feature see this article: Azure Key Vault basic concepts .
Signing using a certificate from Azure Key Vault only works on Windows 10 and above.
Tenant ID
The Azure active directory where Key Vault resides. This field is mandatory!
App ID
The ID of the Azure application that has access to Key Vault. This field is mandatory!
Vault Name
The name of the Key Vault. This field is mandatory!
Certificate Name
The name of the certificate stored in the Key Vault. This field is mandatory!
Certificate Version
A certificate stored in a Key Vault can have multiple versions. The string stored in this field identifies a version.
When this field is empty, Azure Key Vault signs with the latest certificate version.
Client Secret
When a file is signed, the user will be prompted to enter the Client secret associated with the application identified with ID - App ID. The Client secret is not stored in the project file.
Using command line
When using Advanced Installer from command line, you can set the Client secret using the following command:SetAzureKeyVaultSecret
Due to the fact that the Client secret is not stored in the project file, SetAzureKeyVaultSecret command can be used only from a .AIC command file .
For increased security, the Client secret can be stored in an Environment variable using -secret_is_env_var_name switch. With this switch, the command will interpret that the name entered as a parameter is an environment variable.
For security reasons, environment variables can be used in all the above fields instead of the actual values. Environment variables can be easily securitized in Azure Pipelines. For example the actual Tenant Id can be stored in%TenantId% Environment variable. In this case, just enter the the%TenantId% reference in the Tenant Id field. At build time the value stored in this environment variable will resolved and used for the Tenant ID.
The Azure Key Vault certificate subject can be synchronized with the MSIX Publisher ID. To achieve this you must press the Synchronize button from Publisher Section of Package Information page. At build time the subject - publisher ID mismatch is detected automatically.
Use Device Guard for signing
Device Guard signing only works on Windows 10.
To sign a package with Device Guard you need an Azure account configured for Device Guard signing. For more information regarding the configuration see this article:Sign an MSIX package with Device Guard signing
The Publisher ID from Package Information Page must adhere to the following format:CN=account_name.onmicrosoft.com
Using command line
You can set Device Guard sign account name and password using the following command: SetMsActiveDirectoryCredentials.
SetMsActiveDirectoryCredentials command can only be used from a .AIC command file due to the fact that the password is not saved in the project or the registry.
Example of a command file
SetMsActiveDirectoryCredentials -username user_name -password account_password [-password_is_env_var_name]
build -buildslist Build_MSIX_APPX -force
Copy
Optionally, instead of the actual password, you can specify an environment variable where the password is stored, using the optional command line parameter[-password_is_env_var_name]
If the account is not properly configured for Device Guard signing, signing a file could trigger an error that can imply that the timestamp can’t be applied.
Signature Properties
Description
This field contains the signed content’s description. It will be shown by the Windows UAC after you click the “Install” button.
Description URL
This field contains a URL for a complete description of the signed content. The URL will be used when the package is launched from an untrusted location (for example from the network) in the “Open File - Security Warning” dialog, where the “Name” field will become a link to the URL you specified.
Timestamp service URL
A digital certificate has a validity period. After that period expires the signed code is not considered certified anymore. To prevent that a timestamp can be placed at the signing time which will show that the certificate was valid when the signing was done.
The “Timestamp service URL” specifies the URL of the timestamp server. An examples of such server is:
https://www.sectigo.com/resource-library/time-stamping-server .
Signature properties are required to display the exact MSI name on the UAC prompt.
Timestamp delay (ms)
In this field you can configure how many milliseconds Advanced Installer will wait between two consecutive signing operations
Patching
Enable installing of patches for this product without elevation
By enabling this option, you don’t need elevated privileges when applying the patch if both patch and target MSI are signed using the same certificate.
An administrator can disable least-privilege patching on the computer by setting the DisableLUAPatching policy to 1. You can set the MSIDISABLELUAPATCHING property to 1 during the initial installation of an application to prevent least-privilege patching for that application only.
This option is not available for Patch Project .
Did you find this page useful?
Please give it a rating:
Thanks!
Report a problem on this page
Information is incorrect or missing
Information is unclear or confusing
Something else
Can you tell us what’s wrong?
Send message
Also read:
- [New] In 2024, Text Temporal Tinkering Tools
- [New] Mastering Instagram's Most Active Hours for 2024
- [Updated] 2024 Approved Premier Media Mover MP4-to-FB
- [Updated] In 2024, Ultimate #11 List Streaming Audio Recorders Uncovered
- [Updated] Monitor Top YouTube Videos - Select Rank Trackers Guide for 2024
- [Updated] Shifting From Spotify Playlists to Customized YouTube Music Catalogs
- 2024 Approved Step-by-Step Save YouTube Sounds Directly
- 詳盡指南:轻松修复Windows 11鼠标点击不响应问题
- Comment Configurer Et Démarrer Une Sync Bi-Directionnelle Avec AOMEI Backup Sur Mac
- Easy Guide: Downloading Broadcom's Bluetooth Drivers for Your Windows PC (Windows 10, 8 & 7)
- Maximizing Data Retention: Effective Techniques for Enhancing VM Storage Options
- Methoden Zur Zwangsaktivierung Von iCloud-Synchro Auf Dem Mac: Eine Umfassende Anleitung
- Quick and Easy Guide: Transfer Your Entire Hard Disk to a Portable USB Drive
- Récupérer Des Photos Perdus Facilement Avec Ces Logiciels Gratuits: Les 5 Meilleurs Choix Pour Votre Appareil Numérique Photo
- Simple Guide: Removing Windows 11 Updates Effortlessly
- Solving the Issue of Non-Responsive Buttons on Windows 11: Proven Fixes
- The 6 Best SIM Unlock Services That Actually Work On Your Honor Play 8T Device
- The Photographer's Route to Perfectly Trimmed Web Pics for 2024
- ポータブルHDDから失われた情報を完全復元する方法を解説!
- Title: Setup Page – Software Deployment Options & Preferences
- Author: Robert
- Created at : 2024-10-16 04:29:58
- Updated at : 2024-10-17 09:08:54
- Link: https://fox-triigers.techidaily.com/setup-page-software-deployment-options-and-preferences/
- License: This work is licensed under CC BY-NC-SA 4.0.